IP anonymizer risk data
IP anonymizer risk data includes:
- anonymizer detection
- identification of different types of anonymizers
- provider name
- anonymizer confidence
- when we last saw the anonymized network
These data points will only be returned when you pass the IP address as an input to the minFraud Insights and Factors web services. Learn more about passing inputs to minFraud.
The minFraud services can identify many IP addresses that belong to different kinds of anonymizers, from VPNs to TOR exit nodes. End-users may use proxies to anonymize their traffic for a variety of reasons. They may be privacy-conscious web users who do not want their personal information tracked. However, anonymizers may also be attempting to get around geofencing or to hide their identity while engaging in fraud and other malicious activities.
If you are using IP anonymizer risk data to perform manual review, you may be interested in the IP risk reasons. Learn more about IP risk reasons.
You may also be interested in the IP risk score and IP risk snapshot. The IP risk score is available in all minFraud services. Learn more about the IP risk score.
Anonymizer detection
If the IP address passed for a transaction has been flagged as any kind of anonymizer, it will be identified as such in the response. Some customers use IP anonymizers when conducting legitimate transactions, but for many businesses anonymized IP addresses are an indicator of increased risk.
The minFraud services use GeoIP2 data for some anonymizer detection. You can learn more about anonymizer detection in our GeoIP2 support article on anonymizers.
If you feel that a customer’s IP address was incorrectly flagged as an anonymizer, please contact our support team, and we will have our data review team investigate the IP. Please do not ask the customer to contact us directly.
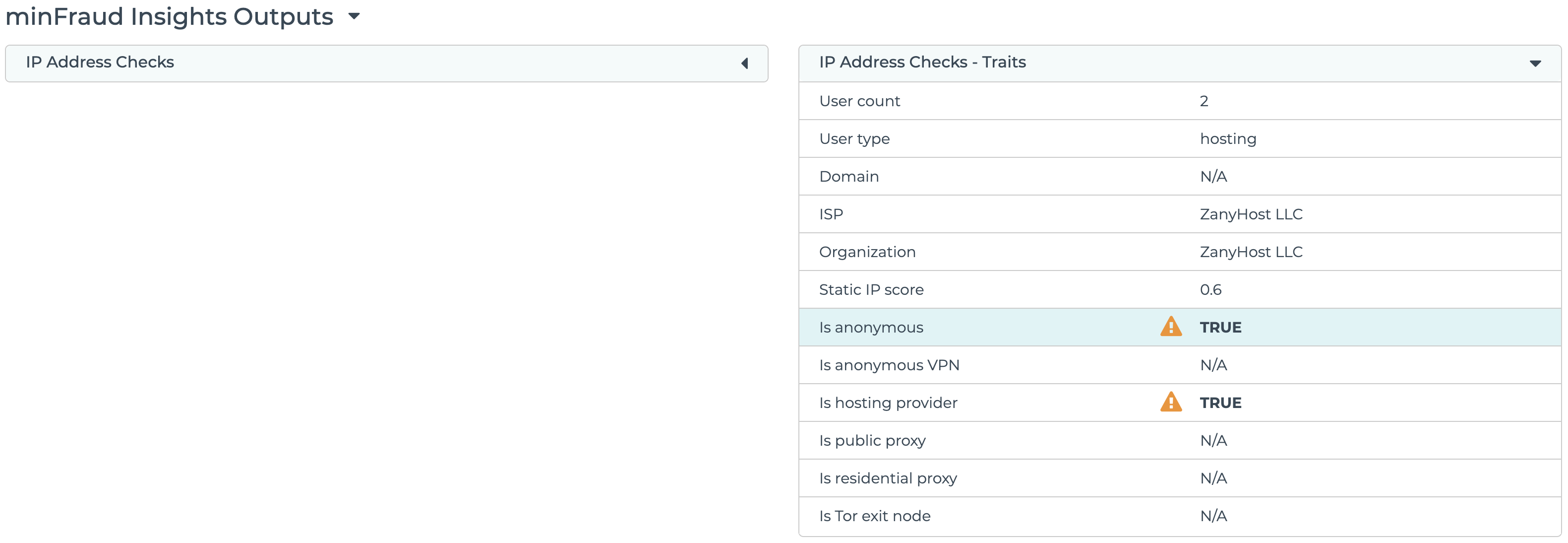
Anonymizer detection is displayed under IP Address Checks - Traits in the transaction review screen in the account portal. Learn how to review transactions using the account portal.
You can read the API specifications for our anonymizer detection on our developer portal:
Types of anonymizers
The minFraud service can detect five different kinds of anonymizers: VPNs, hosting providers, public proxies, residential proxies, and TOR exit nodes.
If you feel that a customer’s IP address was incorrectly flagged as an anonymizer, please contact our support team, and we will have our data review team investigate the IP. Please do not ask the customer to contact us directly.
VPNs
Some customers use IP anonymizers when conducting legitimate transactions, but for many businesses anonymized IP addresses are an indicator of increased risk.
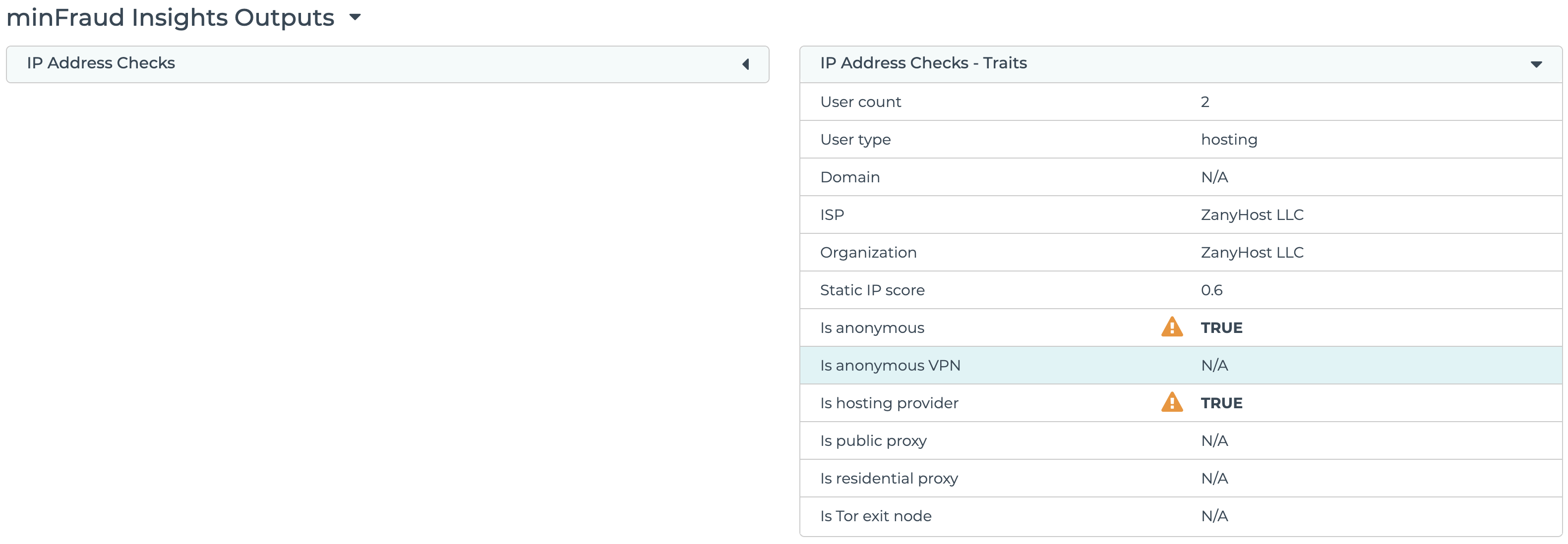
Anonymous VPN detection is displayed under IP Address Checks - Traits in the transaction review screen in the account portal. Learn how to review transactions using the account portal.
You can read the API specifications for our VPN detection on our developer portal:
Hosting providers
Web hosting services can be used to create private proxies, and many VPN services use hosting providers to host their services instead of registering their own IP ranges. This means that if you see traffic associated with an end-user coming from a hosting provider, it may be that the end-user is using a VPN, even if we have not otherwise identified it as such.
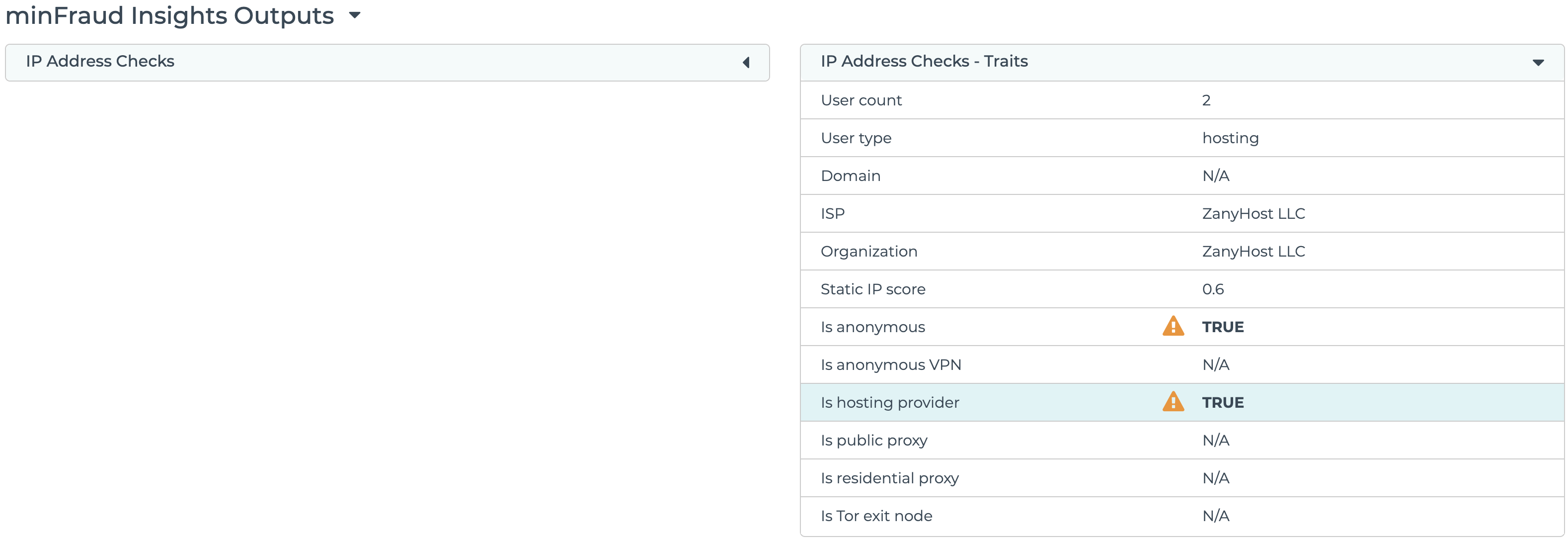
Hosting provider detection is displayed under IP Address Checks - Traits in the transaction review screen in the account portal. Learn how to review transactions using the account portal.
You can read the API specifications for our hosting provider detection on our developer portal:
Public proxies
Public proxies tend to be easy to access and are openly published.
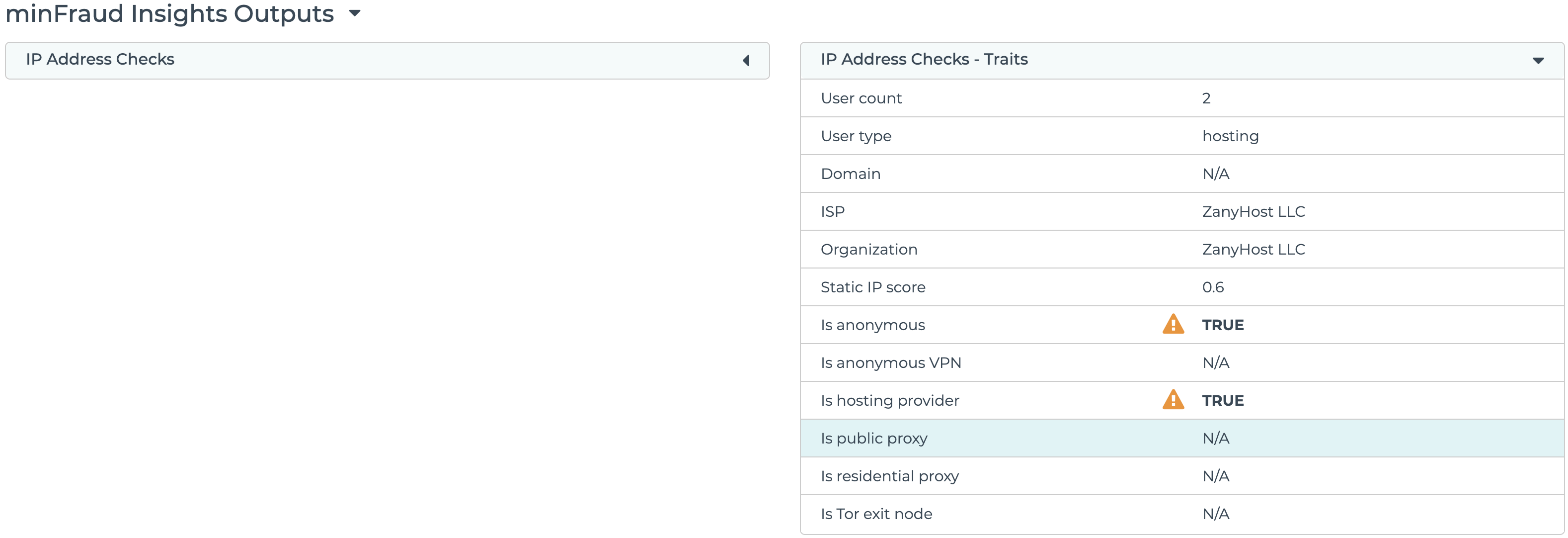
Public proxy detection is displayed under IP Address Checks - Traits in the transaction review screen in the account portal. Learn how to review transactions using the account portal.
You can read the API specifications for our public proxy detection on our developer portal:
Residential proxies
Residential proxies are harder to detect than other kinds of proxies as these IPs appear to be associated with legitimate residential ISPs.
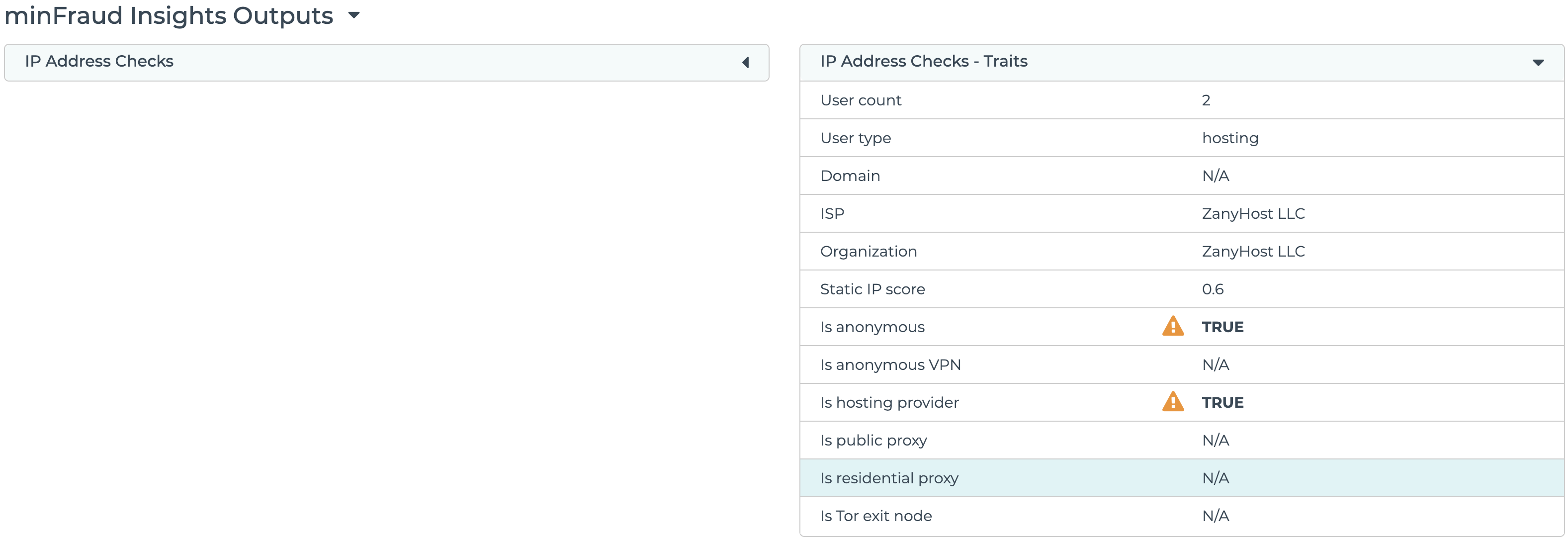
Residential proxy detection is displayed under IP Address Checks - Traits in the transaction review screen in the account portal. Learn how to review transactions using the account portal.
You can read the API specifications for our residential proxy detection on our developer portal:
TOR exit nodes
These are published IPs used as exit nodes for the TOR network. Traffic from these nodes have been relayed through several servers to preserve anonymity.
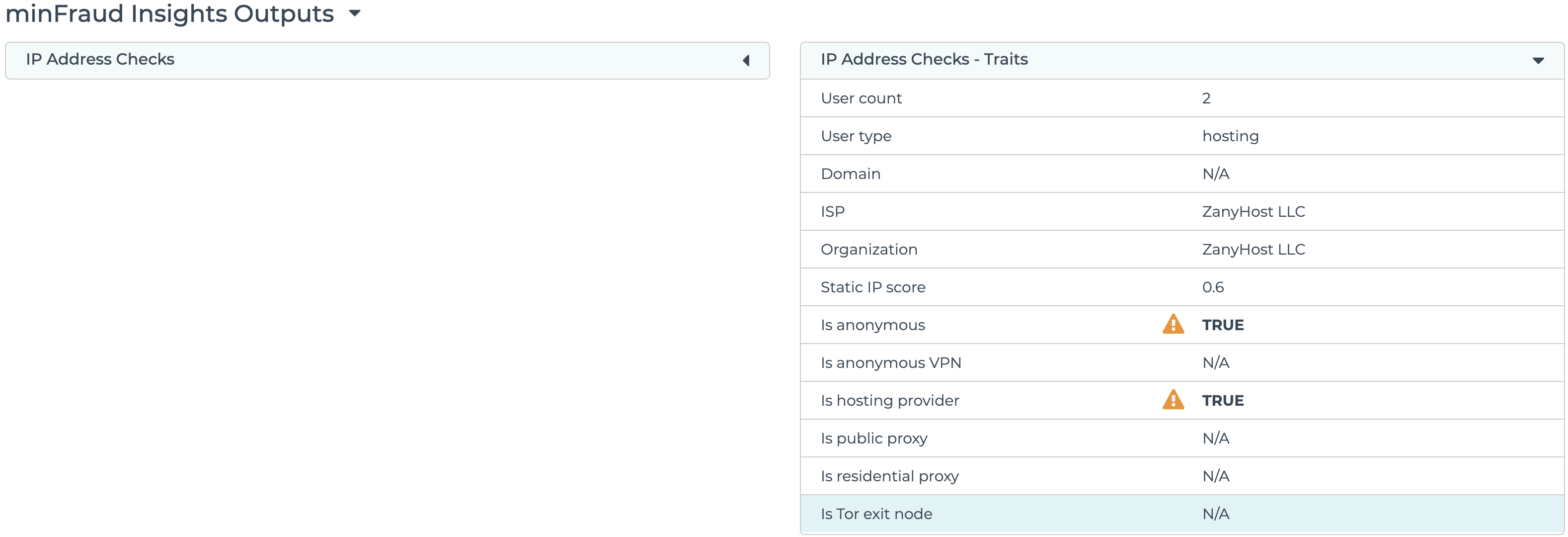
TOR exit node detection is displayed under IP Address Checks - Traits in the transaction review screen in the account portal. Learn how to review transactions using the account portal.
You can read the API specifications for our TOR exit node detection on our developer portal:
Other types of Proxies
In addition to the anonymizers flagged above, there are other kinds of privacy-focused networks such as Apple iCloud Private Relay that protect the identity (and sometimes the more specific geolocation) of the end-user, but include additional oversight by the companies who manage these networks. These networks are identified in our GeoIP2 organization data, which is included in all minFraud Insights and Factors responses. Learn more about these networks and how they are flagged in our GeoIP2 documentation.
Provider name
The name of the VPN provider (e.g., NordVPN, SurfShark, etc.) associated with the network.
Not all anonymous network hosting providers carry the same risks. For example, you can use this field to adjust your blocking to minimize user friction from traffic on corporate VPNs.
You can read the API specifications for provider_name in our developer portal:
Anonymizer confidence
A score (1-99) representing the percent confidence that the network is part of an actively used VPN service.
- High confidence (99): Precise network seen associated with a known anonymizing service
- Medium confidence (30): Network likely associated with a known anonymizing service based on observations
Use these scores to block risky traffic without adding friction for legitimate users. To minimize false positives you may choose to incorporate additional checks to anonymizers with medium confidence.
You can read the API specifications for anonymizer_confidence in our developer portal:
Network last seen
The last day that the network was sighted in our analysis of anonymized networks. This is in the ISO 8601 date format (YYYY-MM-DD).
Since ISPs frequently reallocate IP addresses, if a network on your block list hasn’t been seen in a certain length of time, this field may help you avoid blocking stale threats.
You can read the API specifications for network_last_seen in our developer portal: